Share this
Symmetric vs. Asymmetric Encryption: What's the Difference?
by Brett Daniel on May 4, 2021 9:30:00 AM

Graphic: In this blog post, we discuss the differences between symmetric encryption, a single-key encryption technique, and asymmetric encryption, also known as public-key cryptography, which uses private- and public-key pairs of encryption keys.
To transmit a key or not to transmit a key. That is the question.
There are two main forms of data encryption in use today: symmetric encryption and asymmetric encryption. Every day, when you're using your web browser, responding to emails, submitting website forms, and other activities, symmetric and asymmetric encryption processes are happening, sometimes unbeknownst to you. You may also be familiar with symmetric and asymmetric encryption because you have experience with OpenSSL, key management services, or maybe you've sent an encrypted email or encrypted a Microsoft Word or Adobe PDF file with a password before.
It's important to understand the differences between symmetric and asymmetric encryption and how these security technologies work in the everyday secure transfer of communications. You'll know what these terms mean when you see them, and you'll also be knowledgeable of how they work, their various iterations, aware of their capabilities, and know which is more advisable to implement with regard to securing and authenticating the origin of sensitive information.
In this blog post, we'll discuss the differences between symmetric and asymmetric encryption. At the end, we'll summarize these differences and discuss related encryption options for securing your sensitive data.

Graphic: Symmetric encryption uses a single key to encrypt and decrypt information.
What is symmetric encryption?
Symmetric encryption is a widely used data encryption technique whereby data is encrypted and decrypted using a single, secret cryptographic key.
Specifically, the key is used to encrypt plaintext - the data’s pre-encryption or post-decryption state - and decrypt ciphertext - the data’s post-encryption or pre-decryption state.
Symmetric encryption is one of the most widely used encryption techniques and also one of the oldest, dating back to the days of the Roman Empire. Caesar’s cipher, named after none other than Julius Caesar, who used it to encrypt his military correspondence, is a famous historical example of symmetric encryption in action.
The goal of symmetric encryption is to secure sensitive information. It’s used daily in many major industries, including defense, aerospace, banking, health care, and other industries in which securing a person’s, business’, or organization’s sensitive data is of the utmost importance.
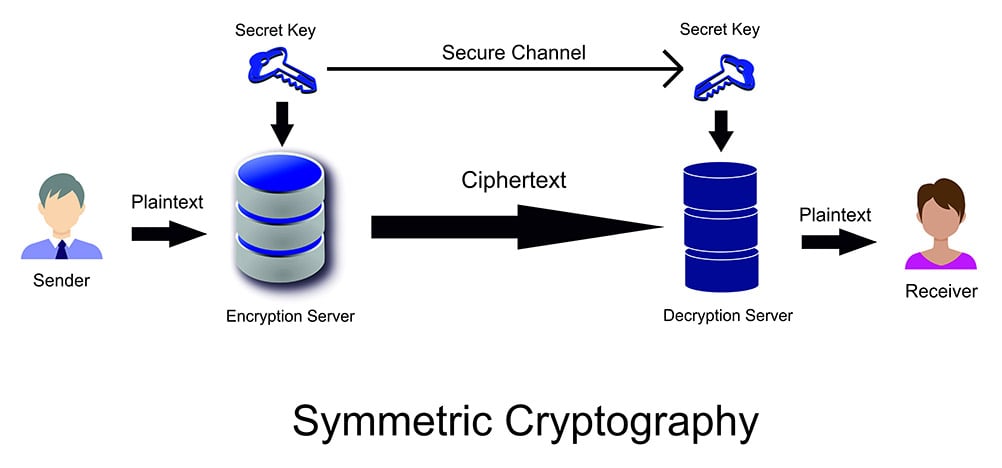
Graphic: This is an illustration of the symmetric encryption process.
How does symmetric encryption work?
Symmetric encryption works by using either a stream cipher or block cipher to encrypt and decrypt data. A stream cipher converts plaintext into ciphertext one byte at a time, and a block cipher converts entire units, or blocks, of plaintext using a predetermined key length, such as 128, 192, or 256 bits.
Senders and recipients using symmetric encryption to transfer data to each other must know the secret key to, in the case of senders, encrypt the data they intend to share with recipients, and in the case of recipients, decrypt and read the encrypted data the senders share with them, as well as encrypt any necessary responses.
Here’s a simplified example of symmetric encryption: if Claire, the sender, wants to send Jacqueline, the recipient, a confidential document, Claire would use the secret key to encrypt the file and send it to Jacqueline, who would be unable to read its contents until she entered the same key that Claire just used to encrypt the file. Conversely, if Jacqueline makes changes to the document and wishes to share them with Claire, she’d use the same key to re-encrypt the file and send it back to Claire, who will use the same key to decrypt the file and access its contents, and the process repeats itself.
Note that this is just an example used to simplify how symmetric encryption works. Symmetric encryption may be carried out manually or automatically.
Symmetric encryption is not limited to the sharing of data between one sender and one recipient, however. Symmetrically encrypted information can be accessed by anyone – Claire, Jacqueline, their co-worker Frank, their boss, Jennifer, et al. – who knows the secret key. Therein lies the reason why concealing the shared cryptographic key from unauthorized parties is vital to the success of symmetric encryption and the integrity of symmetrically encrypted data.
Graphic: Examples of symmetric encryption include the Advanced Encryption Standard (AES) and TLS/SSL protocol.
What are some examples of symmetric encryption?
Popular examples of symmetric encryption include the:
- Data Encryption Standard (DES)
- Triple Data Encryption Standard (Triple DES)
- Advanced Encryption Standard (AES)
- International Data Encryption Algorithm (IDEA)
- TLS/SSL protocol
AES encryption, which uses block ciphers of 128, 192, or 256 bits to encrypt and decrypt data, is one of the most well-known and effective symmetric encryption techniques in use today. It would take billions of years to crack, and that’s why it’s used to secure sensitive information in government, healthcare, banking, and other industries. It is more secure than DES, Triple DES, and IDEA.
DES encryption is now considered by the National Institute of Standards and Technology (NIST) to be a legacy symmetric encryption algorithm because it has long been ineffective at safeguarding sensitive information from brute-force attacks. In fact, the NIST has withdrawn the standard entirely, and its more secure big brother, Triple DES encryption, will have the same fate. Although still in use today, Triple DES encryption is being withdrawn and disallowed by the NIST in 2023 because of mounting security concerns.
IDEA encryption was developed as a replacement for DES in the 1990s, but AES was ultimately deemed more secure. The IDEA is now an open and free block-cipher algorithm, so anyone can use it, but it’s generally considered to be obsolete and ineffective at securing sensitive information today. AES encryption is the gold standard for both purposes.
Transport Layer Security (TLS), as well as its predecessor, Secure Sockets Layer (SSL), uses symmetric encryption. Basically, when a client accesses a server, unique symmetric keys, called session keys, are generated. These session keys are used to encrypt and decrypt the data shared between the client and the server in that specific client-server session at that specific point in time. A new client-server session would generate new, unique session keys.
TLS/SSL uses not only symmetric encryption but both symmetric and asymmetric encryption, to ensure the security of client-server sessions and the information exchanged within them.

Graphic: Advantages of symmetric encryption include security, speed, and industry adoption and acceptance.
What are some advantages of symmetric encryption?
Symmetric encryption is used today because it can encrypt and decrypt large amounts of data quickly, and it's easy to implement. It’s simple to use, and its AES iteration is one of the most secure forms of data encryption available.
Now, symmetric encryption has several advantages over its asymmetric counterpart, but we’ll talk about asymmetric encryption in this blog post a little later.
Some advantages of symmetric encryption include:
- Security: symmetric encryption algorithms like AES take billions of years to crack using brute-force attacks.
- Speed: symmetric encryption, because of its shorter key lengths and relative simplicity compared to asymmetric encryption, is much faster to execute.
- Industry adoption and acceptance: symmetric encryption algorithms like AES have become the gold standard of data encryption because of their security and speed benefits, and as such, have enjoyed decades of industry adoption and acceptance.

Graphic: Disadvantages of symmetric encryption include the need to ensure the security of key distribution mechanisms.
What are some disadvantages of symmetric encryption?
By far the biggest disadvantage of symmetric encryption is its use of a single, secret cryptographic key to encrypt and decrypt information.
Why?
Well, if this secret key is stored in an insecure location on a computer, then hackers could gain access to it using software-based attacks, allowing them to decrypt the encrypted data and thereby defeating the entire purpose of symmetric encryption.
In addition, if one party or entity is encrypting at one location and a separate party or entity decrypting at a second, then the key will need to be transmitted, leaving it vulnerable to interception if the transmission channel is compromised.
That’s why it’s crucial to ensure the security of the encryption key at rest and in transit. Otherwise, you’re just asking for a litany of independent and state-sponsored cyberattackers to access your mission-critical, safety-critical, or legally protected data.
The only other disadvantage to using symmetric encryption is its security efficacy when compared to asymmetric encryption, which is generally considered to be more secure but also slower to execute than symmetric encryption.
But is asymmetric encryption more secure than symmetric encryption? Let’s find out.

Graphic: Asymmetric encryption uses public- and private-key pairs to encrypt and decrypt sensitive information.
What is asymmetric encryption?
Unlike symmetric encryption, which uses the same secret key to encrypt and decrypt sensitive information, asymmetric encryption, also known as public-key cryptography or public-key encryption, uses mathematically linked public- and private-key pairs to encrypt and decrypt senders’ and recipients’ sensitive data.
As with symmetric encryption, plaintext is still converted into ciphertext and vice versa during encryption and decryption, respectively. The main difference is that two unique key pairs are used to encrypt data asymmetrically.
How does asymmetric encryption work?
Here’s a simplified example of asymmetric encryption: if Claire, the sender, and Jacqueline, the recipient, want to continually send a confidential file back and forth to each other, Claire and Jacqueline will give their unique and respective public keys to each other. Claire will then use Jacqueline’s public key to encrypt the file, since it’s intended for Jacqueline only, and send the file to Jacqueline. Upon receipt of the file, Jacqueline will use her private key – keyword, “private,” meaning no one else other than Jacqueline knows it - to decrypt the file and access its contents. No one other than Jacqueline, not even Claire, can decrypt this file, because no one other than Jacqueline knows Jacqueline’s private key. The same process applies when Jacqueline wants to send the file back to Claire. Jacqueline ties it to Claire’s public key, and Claire uses her private key to decrypt the file.
Note that this is a simplification of asymmetric encryption. Like symmetric encryption, asymmetric encryption may be carried out manually or automatically.
Now, do you see how asymmetric encryption could be seen as more secure than symmetric encryption? While this is an interesting inquiry, it’s not the right question to ask, really, because, technically, whether symmetric or asymmetric encryption is more secure depends largely on key size and the security of the media that stores or transmits cryptographic keys.
One reason asymmetric encryption is often regarded as more secure than symmetric encryption is that asymmetric encryption, unlike its counterpart, does not require the exchange of the same encrypt-decrypt key between two or more parties. Yes, public keys are exchanged, but users sharing data in an asymmetric cryptosystem have unique public and private key pairs, and their public keys, because they’re used for encryption only, pose no risk of unauthorized decryption by hackers should they become known, because the hackers, assuming private keys are kept private, don’t know the users’ private keys and thus cannot decrypt the encrypted data.
Asymmetric encryption also allows for digital signature authentication, unlike symmetric encryption. Basically, this involves using private keys to digitally sign messages or files, and their corresponding public keys are used to confirm that these messages originated from the correct, verified sender.

Graphic: Examples of asymmetric encryption include Rivest Shamir Adleman (RSA) and the Digital Signature Algorithm (DSA).
What are some examples of asymmetric encryption?
Examples of asymmetric encryption include:
- Rivest Shamir Adleman (RSA)
- the Digital Signature Standard (DSS), which incorporates the Digital Signature Algorithm (DSA)
- Elliptical Curve Cryptography (ECC)
- the Diffie-Hellman exchange method
- TLS/SSL protocol
Published in 1977, RSA is one of the oldest examples of asymmetric encryption. Developed by Ron Rivest, Adi Shamir, and Leonard Adleman, RSA encryption generates a public key by multiplying two large, random prime numbers together, and using these same prime numbers, generates a private key. From there, standard asymmetric encryption takes place: information is encrypted using the public key and decrypted using the private key.
The DSS, which incorporates the Digital Signature Algorithm (DSA), is the perfect example of asymmetric digital signature authentication. A sender’s private key is used to digitally sign a message or file, and the recipient uses the sender’s corresponding public key to confirm that the signature originated from the correct sender and not a suspicious or unauthorized source.
ECC is an RSA alternative that uses smaller key sizes and mathematical elliptic curves to execute asymmetric encryption. It’s frequently used to digitally sign cryptocurrency transactions; in fact, the popular cryptocurrency Bitcoin uses ECC – the Elliptic Curve Digital Signature Algorithm (ECDSA), to be exact - to digitally sign transactions and ensure that funds are spent by authorized users only. ECC is much faster than RSA in terms of key and signature generation, and many consider it the future of asymmetric encryption, mainly for web traffic and cryptocurrency but for other applications as well.
Diffie-Hellman, one of cryptography’s greatest breakthroughs, is a key exchange method that two parties who have never met can use to exchange public and private key pairs over public, insecure communication channels. Prior to Diffie-Hellman, two parties seeking to encrypt their communications between each other had to physically pre-exchange encryption keys so that both parties could decipher each other’s encrypted messages. Diffie-Hellman made it so that these keys could be securely exchanged over public communication channels, where third parties normally extract sensitive information and encryption keys.
TLS/SSL uses asymmetric encryption to establish a secure client-server session while the client and server are generating symmetric encryption keys. This is known as a TLS handshake. After the TLS handshake is complete, the client-server session keys are used to encrypt the information exchanged in that session.

Graphic: Advantages of asymmetric encryption include digital signature authentication and increased security due to the privacy of decryption keys.
What are some advantages of asymmetric encryption?
Advantages of using asymmetric encryption include:
- Key distribution not necessary: securing key distribution channels has long been a headache in cryptography. Asymmetric encryption eliminates key distribution entirely. The needed public keys are exchanged through public-key servers, and the disclosure of public keys is not, at this time, detrimental to the security of encrypted messages, because they cannot be used to derive private keys.
- Exchange of private keys not necessary: with asymmetric encryption, private keys should remain stored in a secure location and thus private to the entities using them. Basically, the keys needed to decrypt sensitive information are never, and should not ever be, exchanged over a potentially compromised communication channel, and that’s a major plus for the security and integrity of encrypted messages.
- Digital signature/message authentication: with asymmetric encryption, senders can use their private keys to digitally sign and verify that a message or file originated from them and not an untrusted third party.
It may seem like there’s no going wrong with asymmetric encryption. I mean, why would you ever choose symmetric encryption if asymmetric encryption is so secure?
One word: speed.

Graphic: Disadvantages of asymmetric encryption include slowness of execution when compared to symmetric encryption.
What are some disadvantages of asymmetric encryption?
The main disadvantage of asymmetric encryption is that it’s slower than symmetric encryption because of its longer key lengths, not to mention that asymmetric encryption calculations tend to be much more complex than their symmetric counterparts.
Why? Because, in theory, public keys can be used to crack private keys – again, they’re mathematically linked – but asymmetric encryption uses extraordinarily long key lengths to make this virtually impossible, at least for now.
So, in a nutshell, symmetric encryption is faster than asymmetric encryption. Asymmetric encryption sacrifices speed for security, while symmetric encryption sacrifices security for speed.
Now, this is not to say that symmetric encryption is insecure; however, the very foundation of asymmetric encryption eliminates several information security risks that still exist within poorly managed symmetric encryption cryptosystems.

Graphic: Let's summarize the "key" differences between symmetric and asymmetric encryption.
Conclusion: summary of key differences
The key differences between symmetric and asymmetric encryption are speed and security preferences. Generally speaking, symmetric encryption is faster and simpler but is often viewed as less secure than asymmetric encryption. But as we've discussed, encryption really boils down to two things: key size and the security of the media storing encryption keys.
Symmetric encryption is much faster to execute because of its shorter key lengths. Asymmetric encryption has a tendency to bog down networks because of its longer key lengths and complex algorithms. These are the tradeoffs worth considering when deciding which type of encryption to employ.
At Trenton Systems, we offer data encryption solutions in our high-performance servers and workstations in the form of AES-compliant, Opal-compliant, and FIPS-140-2-compliant self-encrypting drives (SEDs).
For more information about how we ensure the integrity of your data using data encryption, reach out to us today.
Share this
- High-performance computers (42)
- Military computers (38)
- Rugged computers (32)
- Cybersecurity (25)
- Industrial computers (25)
- Military servers (24)
- MIL-SPEC (20)
- Rugged servers (19)
- Press Release (17)
- Industrial servers (16)
- MIL-STD-810 (16)
- 5G Technology (14)
- Intel (13)
- Rack mount servers (12)
- processing (12)
- Computer hardware (11)
- Edge computing (11)
- Rugged workstations (11)
- Made in USA (10)
- Partnerships (9)
- Rugged computing (9)
- Sales, Marketing, and Business Development (9)
- Trenton Systems (9)
- networking (9)
- Peripheral Component Interconnect Express (PCIe) (7)
- Encryption (6)
- Federal Information Processing Standards (FIPS) (6)
- GPUs (6)
- IPU (6)
- Joint All-Domain Command and Control (JADC2) (6)
- Server motherboards (6)
- artificial intelligence (6)
- Computer stress tests (5)
- Cross domain solutions (5)
- Mission-critical servers (5)
- Rugged mini PCs (5)
- AI (4)
- BIOS (4)
- CPU (4)
- Defense (4)
- Military primes (4)
- Mission-critical systems (4)
- Platform Firmware Resilience (PFR) (4)
- Rugged blade servers (4)
- containerization (4)
- data protection (4)
- virtualization (4)
- Counterfeit electronic parts (3)
- DO-160 (3)
- Edge servers (3)
- Firmware (3)
- HPC (3)
- Just a Bunch of Disks (JBOD) (3)
- Leadership (3)
- Navy (3)
- O-RAN (3)
- RAID (3)
- RAM (3)
- Revision control (3)
- Ruggedization (3)
- SATCOM (3)
- Storage servers (3)
- Supply chain (3)
- Tactical Advanced Computer (TAC) (3)
- Wide-temp computers (3)
- computers made in the USA (3)
- data transfer (3)
- deep learning (3)
- embedded computers (3)
- embedded systems (3)
- firmware security (3)
- machine learning (3)
- Automatic test equipment (ATE) (2)
- C6ISR (2)
- COTS (2)
- COVID-19 (2)
- CPUs (2)
- Compliance (2)
- Compute Express Link (CXL) (2)
- Computer networking (2)
- Controlled Unclassified Information (CUI) (2)
- DDR (2)
- DDR4 (2)
- DPU (2)
- Dual CPU motherboards (2)
- EW (2)
- I/O (2)
- Military standards (2)
- NVIDIA (2)
- NVMe SSDs (2)
- PCIe (2)
- PCIe 4.0 (2)
- PCIe 5.0 (2)
- RAN (2)
- SIGINT (2)
- SWaP-C (2)
- Software Guard Extensions (SGX) (2)
- Submarines (2)
- Supply chain security (2)
- TAA compliance (2)
- airborne (2)
- as9100d (2)
- chassis (2)
- data diode (2)
- end-to-end solution (2)
- hardware security (2)
- hardware virtualization (2)
- integrated combat system (2)
- manufacturing reps (2)
- memory (2)
- mission computers (2)
- private 5G (2)
- protection (2)
- secure by design (2)
- small form factor (2)
- software security (2)
- vRAN (2)
- zero trust (2)
- zero trust architecture (2)
- 3U BAM Server (1)
- 4G (1)
- 4U (1)
- 5G Frequencies (1)
- 5G Frequency Bands (1)
- AI/ML/DL (1)
- Access CDS (1)
- Aegis Combat System (1)
- Armed Forces (1)
- Asymmetric encryption (1)
- C-RAN (1)
- COMINT (1)
- Cloud-based CDS (1)
- Coast Guard (1)
- Compliance testing (1)
- Computer life cycle (1)
- Containers (1)
- D-RAN (1)
- DART (1)
- DDR5 (1)
- DMEA (1)
- Data Center Modular Hardware System (DC-MHS) (1)
- Data Plane Development Kit (DPDK) (1)
- Defense Advanced Research Projects (DARP) (1)
- ELINT (1)
- EMI (1)
- EO/IR (1)
- Electromagnetic Interference (1)
- Electronic Warfare (EW) (1)
- FIPS 140-2 (1)
- FIPS 140-3 (1)
- Field Programmable Gate Array (FPGA) (1)
- Ground Control Stations (GCS) (1)
- Hardware-based CDS (1)
- Hybrid CDS (1)
- IES.5G (1)
- ION Mini PC (1)
- IP Ratings (1)
- IPMI (1)
- Industrial Internet of Things (IIoT) (1)
- Industry news (1)
- Integrated Base Defense (IBD) (1)
- LAN ports (1)
- LTE (1)
- Life cycle management (1)
- Lockheed Martin (1)
- MIL-S-901 (1)
- MIL-STD-167-1 (1)
- MIL-STD-461 (1)
- MIL-STD-464 (1)
- MOSA (1)
- Multi-Access Edge Computing (1)
- NASA (1)
- NIC (1)
- NIC Card (1)
- NVMe (1)
- O-RAN compliant (1)
- Oil and Gas (1)
- Open Compute Project (OCP) (1)
- OpenRAN (1)
- P4 (1)
- PCIe card (1)
- PCIe lane (1)
- PCIe slot (1)
- Precision timestamping (1)
- Product life cycle (1)
- ROM (1)
- Raytheon (1)
- Remotely piloted aircraft (RPA) (1)
- Rugged computing glossary (1)
- SEDs (1)
- SIM Card (1)
- Secure boot (1)
- Sensor Open Systems Architecture (SOSA) (1)
- Small form-factor pluggable (SFP) (1)
- Smart Edge (1)
- Smart NIC (1)
- SmartNIC (1)
- Software-based CDS (1)
- Symmetric encryption (1)
- System hardening (1)
- System hardening best practices (1)
- TME (1)
- Tech Partners (1)
- Total Memory Encryption (TME) (1)
- Transfer CDS (1)
- USB ports (1)
- VMEbus International Trade Association (VITA) (1)
- Vertical Lift Consortium (VLC) (1)
- Virtual machines (1)
- What are embedded systems? (1)
- Wired access backhaul (1)
- Wireless access backhaul (1)
- accredidation (1)
- aerospace (1)
- air gaps (1)
- airborne computers (1)
- asteroid (1)
- authentication (1)
- autonomous (1)
- certification (1)
- cognitive software-defined radios (CDRS) (1)
- command and control (C2) (1)
- communications (1)
- cores (1)
- custom (1)
- customer service (1)
- customer support (1)
- data linking (1)
- data recording (1)
- ethernet (1)
- full disk encryption (1)
- hardware monitoring (1)
- heat sink (1)
- hypervisor (1)
- in-house technical support (1)
- input (1)
- integrated edge solution (1)
- international business (1)
- licensed spectrum (1)
- liquid cooling (1)
- mCOTS (1)
- microelectronics (1)
- missile defense (1)
- mixed criticality (1)
- moving (1)
- multi-factor authentication (1)
- network slicing (1)
- neural networks (1)
- new headquarters (1)
- next generation interceptor (1)
- non-volatile memory (1)
- operating system (1)
- output (1)
- outsourced technical support (1)
- post-boot (1)
- pre-boot (1)
- private networks (1)
- public networks (1)
- radio access network (RAN) (1)
- reconnaissance (1)
- rugged memory (1)
- secure flash (1)
- security (1)
- self-encrypting drives (SEDs) (1)
- sff (1)
- software (1)
- software-defined radios (SDRs) (1)
- speeds and feeds (1)
- standalone (1)
- storage (1)
- systems (1)
- tactical wide area networks (1)
- technical support (1)
- technology (1)
- third-party motherboards (1)
- troposcatter communication (1)
- unlicensed spectrum (1)
- volatile memory (1)
- vpx (1)
- zero trust network (1)
- January 2025 (1)
- November 2024 (1)
- October 2024 (1)
- August 2024 (1)
- July 2024 (1)
- May 2024 (1)
- April 2024 (3)
- February 2024 (1)
- November 2023 (1)
- October 2023 (1)
- July 2023 (1)
- June 2023 (3)
- May 2023 (7)
- April 2023 (5)
- March 2023 (7)
- December 2022 (2)
- November 2022 (6)
- October 2022 (7)
- September 2022 (8)
- August 2022 (3)
- July 2022 (4)
- June 2022 (13)
- May 2022 (10)
- April 2022 (4)
- March 2022 (11)
- February 2022 (4)
- January 2022 (4)
- December 2021 (1)
- November 2021 (4)
- September 2021 (2)
- August 2021 (1)
- July 2021 (2)
- June 2021 (3)
- May 2021 (4)
- April 2021 (3)
- March 2021 (3)
- February 2021 (8)
- January 2021 (4)
- December 2020 (5)
- November 2020 (5)
- October 2020 (4)
- September 2020 (4)
- August 2020 (6)
- July 2020 (9)
- June 2020 (11)
- May 2020 (13)
- April 2020 (8)
- February 2020 (1)
- January 2020 (1)
- October 2019 (1)
- August 2019 (2)
- July 2019 (2)
- March 2019 (1)
- January 2019 (2)
- December 2018 (1)
- November 2018 (2)
- October 2018 (5)
- September 2018 (3)
- July 2018 (1)
- April 2018 (2)
- March 2018 (1)
- February 2018 (9)
- January 2018 (27)
- December 2017 (1)
- November 2017 (2)
- October 2017 (3)
/Trenton%20Systems%20Circular%20Logo-3.png?width=50&height=50&name=Trenton%20Systems%20Circular%20Logo-3.png)

No Comments Yet
Let us know what you think