Why the Armed Forces Must Prioritize Secure, Made-In-USA GPU Computers
by Robert Haag on May 21, 2021 8:34:43 AM
Graphic: GPU-intensive AI is and will continue to be an integral part of many military deployments. Bearing this in mind, It's crucial that the Armed Forces prioritize the procurement and acquisition of cybersecure, made-in-USA GPU computing platforms that defend the integrity of mili …
Trenton Systems welcomes Robert Haag as Executive Vice President
by Brett Daniel on May 19, 2021 9:31:32 AM
Photo: Robert (Bob) Haag, Trenton Systems' new Executive Vice President Lawrenceville, Georgia, Wednesday, May 19, 2021 - Trenton Systems is pleased to announce and welcome Robert Haag as its new Executive Vice President. Haag will be responsible for working across the company to help …
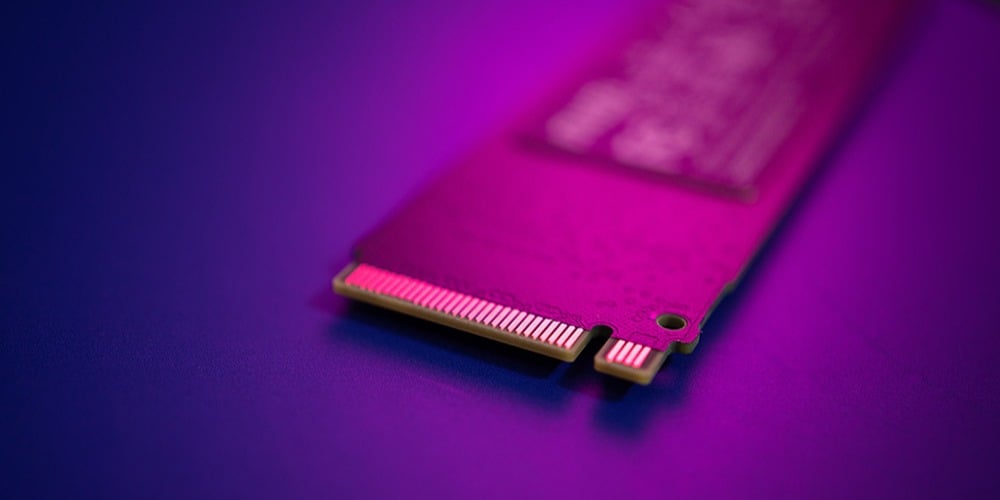
What is NVMe? A Guide to Non-Volatile Memory Express
by Will Shirley on May 13, 2021 11:30:00 AM
Photo: An M.2 NVMe SSD, for used high-speed, PCIe-based reading and writing of data Non-volatile storage media has long been one of the most restrictive bottlenecks in high-performance computing. Humanity generates 2.5 quintillion bytes of data daily. That data has to be stored somewh …
Symmetric vs. Asymmetric Encryption: What's the Difference?
by Brett Daniel on May 4, 2021 9:30:00 AM
Graphic: In this blog post, we discuss the differences between symmetric encryption, a single-key encryption technique, and asymmetric encryption, also known as public-key cryptography, which uses private- and public-key pairs of encryption keys. To transmit a key or not to transmit a …
/Trenton%20Systems%20Circular%20Logo-3.png?width=50&height=50&name=Trenton%20Systems%20Circular%20Logo-3.png)