Share this
Computer Security: Guarding Hardware, Firmware, Software Holistically
by Brett Daniel on Feb 26, 2021 4:00:00 PM
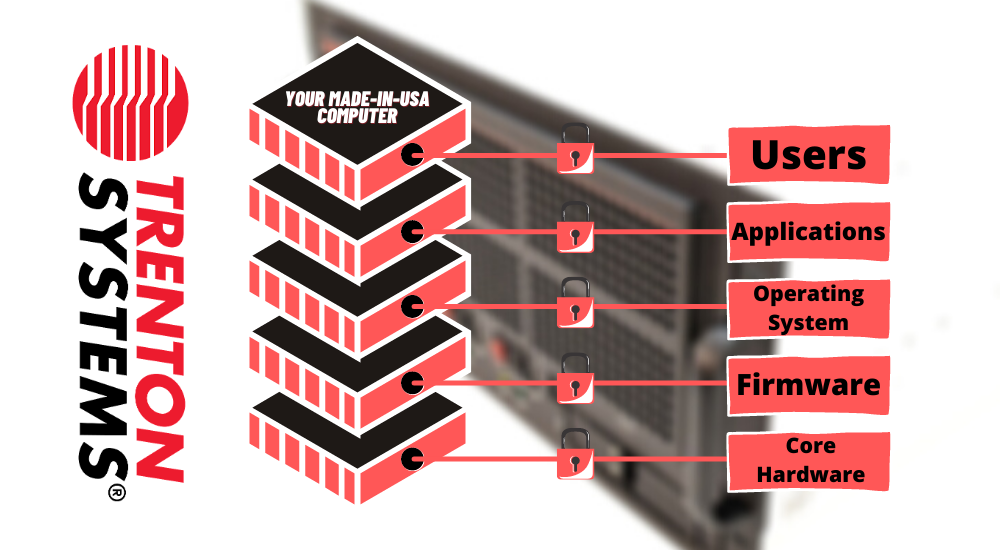
Graphic: Trenton Systems and its security partners strongly believe in comprehensive cybersecurity solutions, starting with the hardware that underlies your server or workstation.
Recent high-profile cyberattacks and shocking revelations about supply chain security are causing military, industrial, and commercial enterprises to rethink, reassess, and rebuild their cybersecurity infrastructure to better protect their sensitive data with the latest technologies and tactics.
Take December 2020's SolarWinds hack, which struck Microsoft, Cisco, Intel, and numerous federal government departments, including the Department of Defense and Department of State. Hackers were able to remain undetected for more than a year while they modified SolarWinds' Orion software update system and executed a covert, clever supply chain attack, the likes of which its victims had never seen.
The COVID-19 pandemic hasn't helped matters on the cybersecurity front, either, with up to as many as 4,000 attacks now being reported to the FBI daily, a 400-percent increase from before the pandemic.
Hackers have begun to shift their attack focus from individuals and small businesses to major corporations, the federal government, and critical infrastructure amid COVID-19 as well. The SolarWinds hack and related incidents are perfect examples. It's readily apparent that large-scale cyberattacks on these crucial institutions are becoming increasingly prevalent.
And nearly 45 percent of decision-makers say that information security has become a greater priority for their organizations since the onset of the pandemic.
It's not difficult to see why. More and more enterprises are sharing more data and becoming increasingly reliant on remote workers and remote networks employing various, sometimes vulnerable, hardware and software combinations, which broadens a cybercriminal's attack surface and provides more avenues into a business's or organization's network.
Considering these figures and others outlined later in this blog post, securing the system stack's "big three" layers - hardware, firmware, and software - holistically is and should continue to be a top priority moving forward.
Attackers are now targeting the lower layers of the computing stack after spending years bombarding the software layers, which, thanks to years of study, investment, and continuous implementation of improvements, have become more challenging for hackers to exploit.
But you didn't think they'd just stop trying, did you?
Now, hackers are hitting hardware and firmware as well as software. Although the software layers have become increasingly difficult to penetrate for a variety of reasons, failure to adequately protect hardware and firmware can still give hackers access to sensitive data stored or circulating within the upper layers, the very layers the industry has spent so much time and money on defending over the years.
Let's talk a little bit more about the importance of securing each layer, a practice sometimes referred to as "securing by design."

Photo: A comprehensive cybersecurity strategy begins with the hardware and supply chain.
Hardware Security
According to a 2019 survey by Dell and Forrester, hardware- and silicon-level exploits are a pervasive threat.
Nearly two-thirds (63 percent) of companies have experienced a data compromise or breach within the past 12 months due to an exploited vulnerability in hardware- or silicon-level security.
The survey also found that most hardware security initiatives implemented by organizations are ineffective.
While the majority of organizations reported hardware and endpoint security measures as their top security priorities for the coming year, when asked specifically about hardware-level defenses and supply chain protections, they admitted they weren't properly prepared to address vulnerabilities at these levels.
Perhaps most concerning is that the survey found that organizations struggle to prevent or address the damage sustained by these attacks. They're turning to hardware security vendors for help, but just 27 percent of organizations surveyed are satisfied with vendor performance.
All this to say: securing the underlying hardware of your server or workstation demands increased attention.
Hardware attacks are often executed during manufacturing or by injecting modified, malicious components or bogus electronic parts into the hardware supply chain.
So, not only could your sensitive data potentially be deleted, altered, or stolen, but the same hardware on which you depend to protect your system could be an unverified, unprotected fake, which not only jeopardizes the security of your system but could also cause a catastrophic failure in the field.
Common hardware attack vectors include:
- Counterfeit electronic parts
- Manufacturing backdoors and supply chain
- Hardware Trojans
Standard preventative and mitigatory measures for hardware attacks include:
- Disabling unused hardware
- Utilizing hardware-based encryption
- Implementing anti-tamper designs
- Thoroughly inspecting and comparing your hardware
- Staying abreast of the latest counterfeit reports
You can also significantly reduce your risk of a hardware-based attack by buying from a computer manufacturer that purchases its supplies from original equipment manufacturers (OEMs), original component manufacturers (OCMs), authorized distributors, and whose products are made in the USA, TAA-compliant, and protected by supply chain security, supplier quality, and counterfeit protection policies and programs.

Photo: Protecting the mediatory layer between your hardware and software is just as essential as protecting the other layers.
Firmware Security
Firmware vulnerabilities are up 750 percent since 2016. Even in just one year, from 2018 to 2019, discoveries of firmware vulnerabilities skyrocketed by 43 percent.
We know we're throwing tons of numbers at you, but it's vital to drive home the gravity of establishing holistic security.
Check this one out:
By 2022, 70 percent of organizations that do not have a firmware upgrade plan in place will be breached due to a firmware vulnerability.
If this sounds like your business or organization, it might be time to put a plan in place sooner rather than later.
After all, good firmware is secure firmware.
Common firmware attack vectors include:
- Infected USB flash drives
- Corrupted storage drives
- Any product with tamper-susceptible firmware
- WiFi, Bluetooth, and other network connectivity mechanisms
- Social engineering tactics, such as leaving infected USB flash drives in parking lots
Firmware attacks are executed by pushing malicious software into lower-level code. Once implemented, this code can:
- Change or destroy existing firmware
- Target your operating system (OS)
- Penetrate applications installed on your computer
Intel's Platform Firmware Resilience (PFR) is an emerging solution that helps protect your server's firmware and validate its integrity. Other solutions include securing your USB ports and staying abreast of the latest firmware updates from manufacturers.
Protecting your firmware, and any other cybersecurity protections you have to test, implement, and manage, is a lot of work. Of course, you could just work with a trusted computing manufacturer that customizes BIOSes and handles all this for you from the moment you start configuring your system.

Photo: Yes, hardware security and firmware security are hot topics right now, but lest we forget to keep our eyes on software security as well.
Software Security
Due to the COVID-19 pandemic, total cybercrime is up 600 percent.
Sixty-nine percent of organizations don't believe the threats they're seeing can be blocked by their antivirus software.
In April 2020, Google blocked 18 million daily malware and phishing emails related to the novel coronavirus.
Roughly 230,000 new malware samples are produced every day - and this is expected to increase.
Business email compromise (BEC) scams, which frequently use spear-phishing attacks, cost organizations $676 million in 2017.
Ransomware attacks worldwide increased by 350 percent in 2018.
Malware and web-based attacks are the two most costly types of attacks. Companies have spent an average of $2.4 million in defense.
And just one more statistic for good measure: more than 18 million websites are infected with malware every week.
Hardware and firmware may be receiving some newfound attention as potential attack targets, but upper-layer software is still vulnerable and susceptible and demands the same amount of focus. It's important that we don't neglect it because of the current spotlight on the others.
Common software attacks include:
- SQL injection
- Cross-site scripting
- Denial-of-Service (DoS)
- Session hijacking
- Man-in-the-middle
- Supply chain attacks, as seen with the SolarWinds hack
Traditional antivirus software is a must-have, of course, but protecting software from exploitation goes beyond mere antivirus programs.
At the end of the day, encryption, secure code signing, and even old-fashioned measures, such as strong password management, remain effective when executed correctly, and multi-factor authentication is the new special-character password.
Other software security protections include:
- Sanitizing inputs to prevent SQL injections
- Using load balancers and IP banning services
- Educating and training employees on browsing secure websites, email-based malware tactics, and effective password management
- Monitoring for changes in software supply chain elements
Services like LastPass can also help you and your business or organization manage your passwords securely and intelligently.
Did you know that, in 43 percent of password-guessing attempts, hackers gain entry just by typing in the username in the password field? It's just that easy for them. Easily guessable passwords are sensitive-data gold mines served up to hackers on silver platters.
Change the passwords, complicate them, and store printed paper copies only. This strategy is not ideal, we know, but at least hackers, once in your system, won't be able to view your passwords in any documents you may have stored them in.
Lastly, buying from a trusted, reputable computer manufacturer that partners with leading cybersecurity companies and incorporates leading technologies - such as Star Lab's Titanium Security Suite - can take a lot of the testing, implementation, management, and pure guesswork out of the software security equation for you.

Photo: Working with caring, passionate engineers who emphasize the security of your servers and workstations will save you time, money, and headaches.
Conclusion: Secure Your System with Trenton
Trenton Systems looks at cybersecurity holistically, focusing on hardware, firmware, and software protections. It's why we:
- Partner with leading software security companies like Star Lab and FUTURA Cyber for Titanium Security Suite and FIPS 140-2 self-encrypting drive management, respectively
- Customize our BIOSes to add security tweaks and enhancements
- Employ Intel PFR, Intel SGX, Intel TME, and related technologies
- Have a Counterfeit Protection Program (CPP) in place
- Perform supplier quality surveys
- Enforce strict revision control
- Pride ourselves in designing, manufacturing, assembling, integrating, testing, and supporting our cybersecure computing solutions in the USA
- And a host of other processes, procedures, and practices you can learn about in our Master List of Trenton Systems' Cybersecurity Advantages & Solutions
If you're interested in acquiring a cybersecure, made-in-USA, high-performance computing solution, manufactured in a secure United States facility, look no further than Trenton Systems.
We've got you covered - to the core.
Share this
- High-performance computers (42)
- Military computers (38)
- Rugged computers (32)
- Cybersecurity (25)
- Industrial computers (25)
- Military servers (24)
- MIL-SPEC (20)
- Rugged servers (19)
- Press Release (17)
- Industrial servers (16)
- MIL-STD-810 (16)
- 5G Technology (14)
- Intel (13)
- Rack mount servers (12)
- processing (12)
- Computer hardware (11)
- Edge computing (11)
- Rugged workstations (11)
- Made in USA (10)
- Partnerships (9)
- Rugged computing (9)
- Sales, Marketing, and Business Development (9)
- Trenton Systems (9)
- networking (9)
- Peripheral Component Interconnect Express (PCIe) (7)
- Encryption (6)
- Federal Information Processing Standards (FIPS) (6)
- GPUs (6)
- IPU (6)
- Joint All-Domain Command and Control (JADC2) (6)
- Server motherboards (6)
- artificial intelligence (6)
- Computer stress tests (5)
- Cross domain solutions (5)
- Mission-critical servers (5)
- Rugged mini PCs (5)
- AI (4)
- BIOS (4)
- CPU (4)
- Defense (4)
- Military primes (4)
- Mission-critical systems (4)
- Platform Firmware Resilience (PFR) (4)
- Rugged blade servers (4)
- containerization (4)
- data protection (4)
- virtualization (4)
- Counterfeit electronic parts (3)
- DO-160 (3)
- Edge servers (3)
- Firmware (3)
- HPC (3)
- Just a Bunch of Disks (JBOD) (3)
- Leadership (3)
- Navy (3)
- O-RAN (3)
- RAID (3)
- RAM (3)
- Revision control (3)
- Ruggedization (3)
- SATCOM (3)
- Storage servers (3)
- Supply chain (3)
- Tactical Advanced Computer (TAC) (3)
- Wide-temp computers (3)
- computers made in the USA (3)
- data transfer (3)
- deep learning (3)
- embedded computers (3)
- embedded systems (3)
- firmware security (3)
- machine learning (3)
- Automatic test equipment (ATE) (2)
- C6ISR (2)
- COTS (2)
- COVID-19 (2)
- CPUs (2)
- Compliance (2)
- Compute Express Link (CXL) (2)
- Computer networking (2)
- Controlled Unclassified Information (CUI) (2)
- DDR (2)
- DDR4 (2)
- DPU (2)
- Dual CPU motherboards (2)
- EW (2)
- I/O (2)
- Military standards (2)
- NVIDIA (2)
- NVMe SSDs (2)
- PCIe (2)
- PCIe 4.0 (2)
- PCIe 5.0 (2)
- RAN (2)
- SIGINT (2)
- SWaP-C (2)
- Software Guard Extensions (SGX) (2)
- Submarines (2)
- Supply chain security (2)
- TAA compliance (2)
- airborne (2)
- as9100d (2)
- chassis (2)
- data diode (2)
- end-to-end solution (2)
- hardware security (2)
- hardware virtualization (2)
- integrated combat system (2)
- manufacturing reps (2)
- memory (2)
- mission computers (2)
- private 5G (2)
- protection (2)
- secure by design (2)
- small form factor (2)
- software security (2)
- vRAN (2)
- zero trust (2)
- zero trust architecture (2)
- 3U BAM Server (1)
- 4G (1)
- 4U (1)
- 5G Frequencies (1)
- 5G Frequency Bands (1)
- AI/ML/DL (1)
- Access CDS (1)
- Aegis Combat System (1)
- Armed Forces (1)
- Asymmetric encryption (1)
- C-RAN (1)
- COMINT (1)
- Cloud-based CDS (1)
- Coast Guard (1)
- Compliance testing (1)
- Computer life cycle (1)
- Containers (1)
- D-RAN (1)
- DART (1)
- DDR5 (1)
- DMEA (1)
- Data Center Modular Hardware System (DC-MHS) (1)
- Data Plane Development Kit (DPDK) (1)
- Defense Advanced Research Projects (DARP) (1)
- ELINT (1)
- EMI (1)
- EO/IR (1)
- Electromagnetic Interference (1)
- Electronic Warfare (EW) (1)
- FIPS 140-2 (1)
- FIPS 140-3 (1)
- Field Programmable Gate Array (FPGA) (1)
- Ground Control Stations (GCS) (1)
- Hardware-based CDS (1)
- Hybrid CDS (1)
- IES.5G (1)
- ION Mini PC (1)
- IP Ratings (1)
- IPMI (1)
- Industrial Internet of Things (IIoT) (1)
- Industry news (1)
- Integrated Base Defense (IBD) (1)
- LAN ports (1)
- LTE (1)
- Life cycle management (1)
- Lockheed Martin (1)
- MIL-S-901 (1)
- MIL-STD-167-1 (1)
- MIL-STD-461 (1)
- MIL-STD-464 (1)
- MOSA (1)
- Multi-Access Edge Computing (1)
- NASA (1)
- NIC (1)
- NIC Card (1)
- NVMe (1)
- O-RAN compliant (1)
- Oil and Gas (1)
- Open Compute Project (OCP) (1)
- OpenRAN (1)
- P4 (1)
- PCIe card (1)
- PCIe lane (1)
- PCIe slot (1)
- Precision timestamping (1)
- Product life cycle (1)
- ROM (1)
- Raytheon (1)
- Remotely piloted aircraft (RPA) (1)
- Rugged computing glossary (1)
- SEDs (1)
- SIM Card (1)
- Secure boot (1)
- Sensor Open Systems Architecture (SOSA) (1)
- Small form-factor pluggable (SFP) (1)
- Smart Edge (1)
- Smart NIC (1)
- SmartNIC (1)
- Software-based CDS (1)
- Symmetric encryption (1)
- System hardening (1)
- System hardening best practices (1)
- TME (1)
- Tech Partners (1)
- Total Memory Encryption (TME) (1)
- Transfer CDS (1)
- USB ports (1)
- VMEbus International Trade Association (VITA) (1)
- Vertical Lift Consortium (VLC) (1)
- Virtual machines (1)
- What are embedded systems? (1)
- Wired access backhaul (1)
- Wireless access backhaul (1)
- accredidation (1)
- aerospace (1)
- air gaps (1)
- airborne computers (1)
- asteroid (1)
- authentication (1)
- autonomous (1)
- certification (1)
- cognitive software-defined radios (CDRS) (1)
- command and control (C2) (1)
- communications (1)
- cores (1)
- custom (1)
- customer service (1)
- customer support (1)
- data linking (1)
- data recording (1)
- ethernet (1)
- full disk encryption (1)
- hardware monitoring (1)
- heat sink (1)
- hypervisor (1)
- in-house technical support (1)
- input (1)
- integrated edge solution (1)
- international business (1)
- licensed spectrum (1)
- liquid cooling (1)
- mCOTS (1)
- microelectronics (1)
- missile defense (1)
- mixed criticality (1)
- moving (1)
- multi-factor authentication (1)
- network slicing (1)
- neural networks (1)
- new headquarters (1)
- next generation interceptor (1)
- non-volatile memory (1)
- operating system (1)
- output (1)
- outsourced technical support (1)
- post-boot (1)
- pre-boot (1)
- private networks (1)
- public networks (1)
- radio access network (RAN) (1)
- reconnaissance (1)
- rugged memory (1)
- secure flash (1)
- security (1)
- self-encrypting drives (SEDs) (1)
- sff (1)
- software (1)
- software-defined radios (SDRs) (1)
- speeds and feeds (1)
- standalone (1)
- storage (1)
- systems (1)
- tactical wide area networks (1)
- technical support (1)
- technology (1)
- third-party motherboards (1)
- troposcatter communication (1)
- unlicensed spectrum (1)
- volatile memory (1)
- vpx (1)
- zero trust network (1)
- January 2025 (1)
- November 2024 (1)
- October 2024 (1)
- August 2024 (1)
- July 2024 (1)
- May 2024 (1)
- April 2024 (3)
- February 2024 (1)
- November 2023 (1)
- October 2023 (1)
- July 2023 (1)
- June 2023 (3)
- May 2023 (7)
- April 2023 (5)
- March 2023 (7)
- December 2022 (2)
- November 2022 (6)
- October 2022 (7)
- September 2022 (8)
- August 2022 (3)
- July 2022 (4)
- June 2022 (13)
- May 2022 (10)
- April 2022 (4)
- March 2022 (11)
- February 2022 (4)
- January 2022 (4)
- December 2021 (1)
- November 2021 (4)
- September 2021 (2)
- August 2021 (1)
- July 2021 (2)
- June 2021 (3)
- May 2021 (4)
- April 2021 (3)
- March 2021 (3)
- February 2021 (8)
- January 2021 (4)
- December 2020 (5)
- November 2020 (5)
- October 2020 (4)
- September 2020 (4)
- August 2020 (6)
- July 2020 (9)
- June 2020 (11)
- May 2020 (13)
- April 2020 (8)
- February 2020 (1)
- January 2020 (1)
- October 2019 (1)
- August 2019 (2)
- July 2019 (2)
- March 2019 (1)
- January 2019 (2)
- December 2018 (1)
- November 2018 (2)
- October 2018 (5)
- September 2018 (3)
- July 2018 (1)
- April 2018 (2)
- March 2018 (1)
- February 2018 (9)
- January 2018 (27)
- December 2017 (1)
- November 2017 (2)
- October 2017 (3)
/Trenton%20Systems%20Circular%20Logo-3.png?width=50&height=50&name=Trenton%20Systems%20Circular%20Logo-3.png)

No Comments Yet
Let us know what you think